Radio Encryption: The Evolution
Radio Encryption: The Evolution
The theory behind using codes as a form of encryption is age-old. The ancient Spartans are known to have used a form of cryptography called a ‘scytale’ essentially a strip of paper wrapped around a baton. The paper was then unwound and appeared as a random list of letters unless wrapped around the same sized baton. This illustrates the fundamental aspect of encryption: only the sender and the receiver have knowledge of the specific ‘key’ that unlocks the message.
Jumping ahead to the age of wireless communications, very early radio voice transmissions were not very clear and the use of Morse code improved the likelihood of messages being correctly received and understood. As the popularity of wireless communications increased, so did concerns for security. Transmitting over the air, by way of broadcast, meant that messages could be easily intercepted and fall into unintended hands. So wireless transmitters turned to the age-old espionage tricks of codes and ciphers.
These codes evolved from simple substitution codes to single use code phrases with security measures and identification prefixing the message itself. These were all coded by operatives in the field who were under immense pressure. This meant that mistakes were bound to be made with messages sometimes needing to be repeatedly transmitted exposing field operatives for extended periods of time. This gave military opponents extra time to both break the cipher and catch undercover operatives. These operator codes were quickly replaced with mechanically generated encoding such as the German Enigma machine which significantly decreased the time operatives were in the open and decreased the chances of the codes being broken.
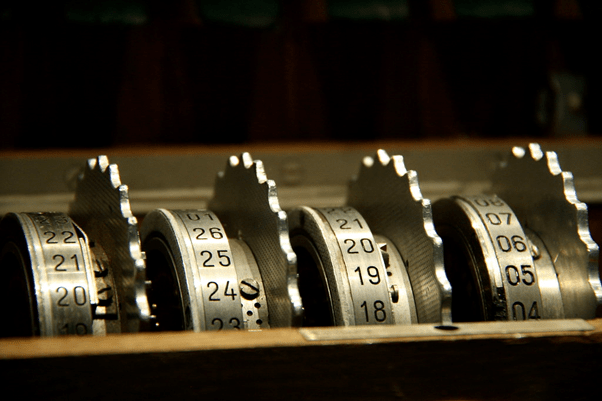
In the modern era, ciphers, codes and keys are generated digitally offering much higher levels of security. These keys – along with multiple other levels of encryption – combine to make encrypted voice over HF radio unintelligible to any listener without the correct key. The keys are now longer – 56 characters for DES-56 encryption or 256 characters for AES-256 encryption – and more complex, forming only one part of the encryption process.
Barrett Communications offers two tiers of encryption for their HF transceivers. The lower tier DES-56 encryption is non-export controlled and suitable for non-classified, time-critical information transfer e.g. orders that will become irrelevant in less than 24 hours.
The upper tier of encryption offered by Barrett is export-controlled US Federal Standard AES-256 encryption. This encryption offers greater security than DES-56 and is suitable for the transfer of classified information.
Both encryption tiers can be combined with Barrett’s Frequency Hopping option, significantly increasing the level of information security.







